Motivate your sales force and optimize sales activities with the right sales tools.
Create and send professional marketing emails or personalized newsletters, then track and analyze the user activities.
The primary goal of customer relationship management systems is to integrate and automate sales, marketing, and customer support.
Contact us for help, support or advice from technical questions. Don’t forget to check out our FAQs, free downloads and blog.
Have full transparency and peace of mind on when and how your business data is being used.
Eliminate borrowing busywork by automating repetitive administrative tasks.
Visualizing report data gives viewers a quick way of digesting information, and online charts provide up-to-date details when you need them.
In software engineering, a software development process is the process of dividing software development work into distinct phases to improve design, product management, and project management. It is also known as a software development life cycle (SDLC). The methodology may include the pre-definition of specific deliverables and artifacts that are created and completed by a project team to develop or maintain an application.
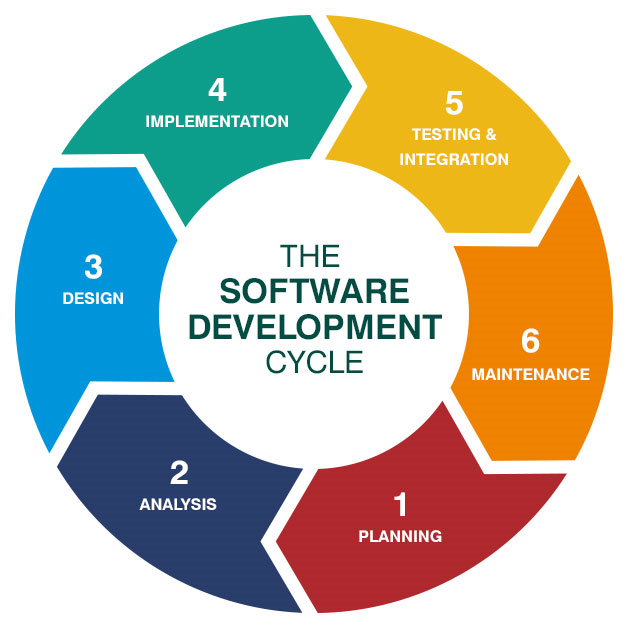
Like with any project, before beginning your team should understand the end goal, the value to the organization or client, and how it will be achieved.
Detailed analysis of the software is performed to identify overall requirements of client. This step is necessary to make adjustments and to ensure that software functions properly at the end.
Once the analysis is complete, the step of designing takes over, which is basically building the architecture of the project. This step helps remove possible flaws by setting a standard and attempting to stick to it.
This stage is crucial for running the developed software assessed by all the stakeholders. This is to ensure the complete level of customer satisfaction.
The testing stage assesses the software for errors and documents bugs if there are any.
Once the software passes through all the stages without any issues, a maintenance process is followed wherein it will be maintained and upgraded from time to time to adapt to changes.
It is a process of mapping the conceptual model to the structures of target DBMS.
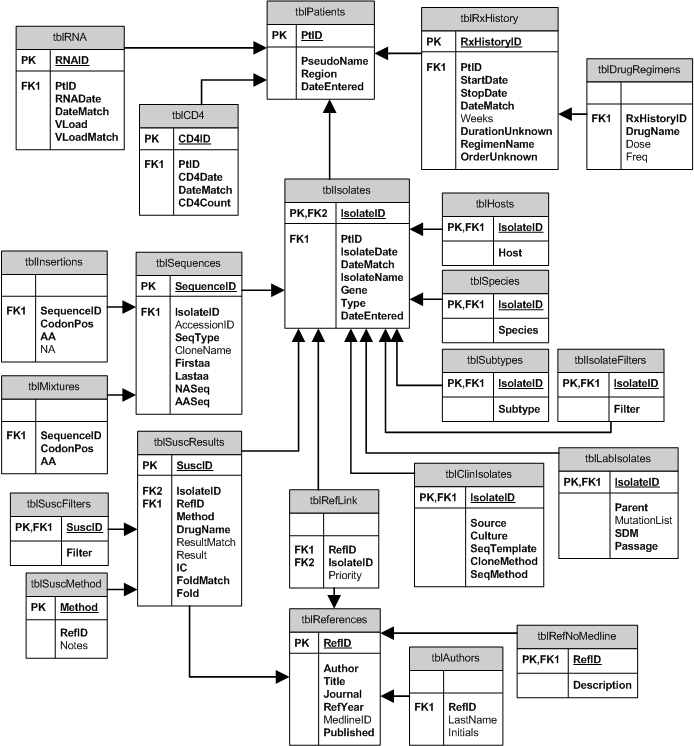
Develop a logical data model for each known user interface for the application using normalization principles.
Combine normalized data requirements from all user interfaces into one consolidated logical database model (view integration).
Translate the conceptual E-R data model for the application into normalized data requirements.
Compare the consolidated logical database design with the translated E-R model and produce one final logical database model for the application.
SOLID is an acronym for the first five object-oriented design (OOD) principles by Robert C. Martin (also known as Uncle Bob).
These principles establish practices that lend to developing software with considerations for maintaining and extending as the project grows. Adopting these practices can also contribute to avoiding code smells, refactoring code, and Agile or Adaptive software development.
SOLID stands for:
In programming, the Single Responsibility Principle (SRP) states that every module or class should have responsibility over a single part of the functionality provided by the software.
In programming, the Open/closed Principle (OCP) states that software entities (classes, modules, functions, etc.) should be open for extensions, but closed for modification.
The Liskov Substitution Principle (LSP) is a fundamental principle in object-oriented programming that states that objects of a superclass should be able to be replaced with objects of a subclass without affecting the correctness of the program.
In programming, the Interface Segregation Principle (ISP) states that no client should be forced to depend on methods it does not use. Put more simply: Do not add additional functionality to an existing interface by adding new methods. Instead, create a new interface and let your class implement multiple interfaces if needed.
In programming, the Dependency Inversion Principle (DIP) is a way to decouple software modules. This principle states that
APIs (application programming interfaces) come in many forms. API designers can choose from a range of protocols and standards when creating a new API, depending on the type of API they are creating, and its purpose. There are meny alternatives available:
Most APIs use representational state transfer (REST), which incorporates the following guidelines:
The client makes a request, and the server responds. This is the only way the two can interact.
Each interaction is new and independent, and the server doesn’t remember previous requests.
A common protocol governs requests and responses.
Requests and responses must maintain their formatting when passing through additional layers between the client and the API.
A response to a request should dictate if the resource can be cached and for how long.
The resulting APIs may be called “REST APIs” or “RESTful APIs.” They’re usually lightweight, scalable, and user friendly.
Simple Object Access Protocol (SOAP) is a data transmission protocol that some APIs use. A SOAP API relies on an XML format and typically receives requests through HTTP. This protocol clearly defines how messages are sent and what information is included, making SOAP APIs more secure but also more difficult to implement.
Remote Procedure Call (RPC) is a protocol that executes scripts on a server via calls that use either JSON or XML. Since the API security and capabilities are limited, RPC APIs are less common than RESTful APIs and SOAP APIs. That said, they may be appropriate for some internal systems.
Web APIs are APIs that can be accessed using the HTTP protocol. The API defines endpoints, and valid request and response formats. Web APIs include the APIs used to communicate with the browser (see list). They may be services such as web notifications and web storage. Different web APIs feature varying levels of security and privacy, including open, internal and partner APIs. Multiple web APIs can be combined into a composite API - a collection of data or service APIs.
Open APIs, also known as external or public APIs, are available to developers and other users with minimal restrictions. They may require registration, and use of an API key, or may be completely open. They are intended for external users (developers at other companies, for example) to access data or services. As an example, take a look at the provided by the UK government. Any developer can access it, without even registering, allowing app builders to include governmental data on restaurant standards in their apps.
In contrast to open APIs, internal APIs are designed to be hidden from external users. They are used within a company to share resources. They allow different teams or sections of a business to consume each other’s tools, data and programs. Using internal APIs has several advantages over conventional integration techniques, including security and access control, an audit trail of system access, and a standard interface for connecting multiple services.
Partner APIs are technically similar to open APIs, but they feature restricted access, often controlled through a third-party API gateway. They are usually intended for a specific purpose, such as providing access to a paid-for service. This is a very common pattern in software as a service ecosystem.
Composite APIs allow developers to access several endpoints in one call. These could be different endpoints of a single API, or they could be multiple services or data sources. Composite APIs are especially useful in microservice architectures, where a user may need information from several services to perform a single task. Using composite APIs can reduce server load and improve application performance, as one call can return all the data a user needs.
REST is acronym for REpresentational State Transfer. It is architectural style for distributed hypermedia systems and was first presented by Roy Fielding in 2000.
{p1}
Essensial WebOffice modules to Start Building Your Business.
{description}
Use SWOT Analysis to assess your organization's current position before you decide on any new strategy.
What do you do well?
What unique resources can you draw on?
What do others see as your strengths?
What could you improve?
Where do you have fewer resources than others?
What are others likely to see as weaknesses?
What opportunities are open to you?
What trends could you take advantage of?
How can you turn your strengths into opportunities?
What threats could harm you?
What is your competition doing?
What threats do your weaknesses expose you to?
Why are specific name given to the products? How do I name my product?
Every brand has a story. And the name has of course been significant in these brands' success. Their name is now their fame!
Brand synergy: Ensure your product name aligns with your brand identity and overall strategy.
Resonance: Your product name must resonate with your ideal customer, evoking the desired feeling, perception, or impression.
Scalability: Think long-term. Do you see this being a stand-alone product or if it’s successful, could it grow into a larger product line? If you envision the latter, you’ll want to take that into consideration when choosing a name.
Visibility: If people can’t easily find and search for your product online, consider it dead on arrival.
Distinctiveness: Competition will be fierce. You want a name that will make your product stand out from the crowd.
Longevity: Don’t be tempted to use the latest fad as inspiration for your new product name. Ask yourself, “will this name make sense to people in 20 years?”
Simplicity: Sometimes, we misspell something and Google figures out what we meant and points us in the right direction. But do you really want to leave it up to chance? Make sure your product name isn’t too difficult to spell or pronounce; otherwise, people will have a hard time finding it and talking about it. Make it easy for your audience.
Your product name should just sound cool (although that doesn’t hurt), its primary job is to guide your ideal customer to buy it, by showing them why it’s the right choice for them.
If you’re in the market for a new laptop and because you carry it in your backpack all day, being lightweight is the most important feature for you, would you go for a MacBook Pro or a MacBook Air? There’s a clear winner here.
The name of your product should also instill confidence in your brand. This is accomplished with consistency. If all of your product names sound like iPhone, iPad, iTunes, and you suddenly launch a new music service called “Streamy,” it’s going to sound random and could potentially cause your customers to lose trust in the brand.
Lastly, your product name should help your brand to generate buzz. You want your name to be the one that turns generic items into something specific. Think of brands that have made a mark. How many of us ask for a Kleenex, even if we’re reaching for a generic brand of facial tissue?
No, names can't be copyrighted, but, depending on where they live, celebrity names may be protected.
In California State, celebrity names are protected even after their death by the California Celebrities Rights Act - Wikipedia (Hollywood is in California after all.)
But the vast majority of actors don't register their names as trademarks (including Tom Cruise, Julia Roberts, and Dustin Hoffman) because there's usually little need for trademark rights for movie actors unless they are offering a non-entertainment business such as a line of perfume or fish and chips.
If you trademark your domain name, you have legal protection if someone uses your trademarked name. If you register your domain names, but don't use your website to sell your products and you don't trademark the name, there isn't anything you can do to stop the other company.
There is only one boss. The customer.
{quote}
{title}
Motivated developers move projects forward more than anyone else.




We offer services focused on making IT support processes more effective and seamless - because that’s what every business needs for smooth operation.
The purpose of an FAQ is generally to provide information on frequent questions or concerns.
{answer}
Follow NET-Builder’s blog for the latest official news and events.
{text}
September 2003
Desktop MLM software, small and large logo.
November 2004

Online liability insurance calculation app Logo.
October 2005
This is the veri first version of NET-Builder Logo.
November 2006
This is the redesigned version.
July 2007

This is the widely used main Logo over years.
December 2008

This is the greeting card version for Cristmas.
September 2009

This is the first logo with reflection of background.
September 2009




This was a concept version.
July 2020
This is a New Generation Logo. After long-long years, there is a simple and fresh design. The color of the schevron changed to red on the top. The globe was changed to flat color background on bottom.
July 2020
This is a New Generation Logo landscape version.
July 2020
This is a New Generation Logo. White background logo.
July 2020
This is the first 3D logo with dak background, rounded cornes, full text and red chevron.
July 2020
This is the full rounded 3D Logo.
July 2020
This is a 3D Logo with incressed corner radius.
July 2020
This is a New Generation Logo with luminescent text outline.
July 2020
This is a New Generation Logo. The text changed simple to NB.
July 2020
The background changed to flat color.
July 2020
The outline changed to leef shape.
July 2020
The background changed to golden texture and the text color changed to blue.
July 2020
Implemented an inline genealogy image.
July 2020
Implemented an inline genealogy image.
July 2020
Implemented an inline genealogy image and logo text.
July 2020
The background changed to golden texture and the text color changed to blue.
July 2020
The background changed to dakt blue and the text color changed to blue & white.
July 2020
This is a 3DLogo with simpel NB text.
August 2021
The background color is white and the text color is blue.
August 2021
The background color is white and the text color is blue.
August 2021
The background color is white and the text color is blue. The text only N.
Contact us for help, support or advice from technical questions. Don’t forget to check out our FAQs, free downloads and blog.
This Privacy Policy document contains types of information that is collected and recorded by NET-Builder and how we use it.
At NET-Builder, accessible from netbuilderglobal.com, one of our main priorities is the privacy of our visitors. This Privacy Policy document contains types of information that is collected and recorded by NET-Builder and how we use it.
If you have additional questions or require more information about our Privacy Policy, do not hesitate to contact us.
NET-Builder follows a standard procedure of using log files. These files log visitors when they visit websites. All hosting companies do this and a part of hosting services' analytics. The information collected by log files include internet protocol (IP) addresses, browser type, Internet Service Provider (ISP), date and time stamp, referring/exit pages, and possibly the number of clicks. These are not linked to any information that is personally identifiable. The purpose of the information is for analyzing trends, administering the site, tracking users' movement on the website, and gathering demographic information. Our Privacy Policy was created with the help of the Privacy Policy Generator and the Privacy Policy Generator.
Like any other website, NET-Builder uses 'cookies'. These cookies are used to store information including visitors' preferences, and the pages on the website that the visitor accessed or visited. The information is used to optimize the users' experience by customizing our web page content based on visitors' browser type and/or other information.
For more general information on cookies, please read the "What Are Cookies" article on Cookie Consent website.
Google is one of a third-party vendor on our site. It also uses cookies, known as DART cookies, to serve ads to our site visitors based upon their visit to www.website.com and other sites on the internet. However, visitors may choose to decline the use of DART cookies by visiting the Google ad and content network Privacy Policy at the following URL – https://policies.google.com/technologies/ads
Some of advertisers on our site may use cookies and web beacons. Our advertising partners are listed below. Each of our advertising partners has their own Privacy Policy for their policies on user data. For easier access, we hyperlinked to their Privacy Policies below.
You may consult this list to find the Privacy Policy for each of the advertising partners of NET-Builder.
Third-party ad servers or ad networks uses technologies like cookies, JavaScript, or Web Beacons that are used in their respective advertisements and links that appear on NET-Builder, which are sent directly to users' browser. They automatically receive your IP address when this occurs. These technologies are used to measure the effectiveness of their advertising campaigns and/or to personalize the advertising content that you see on websites that you visit.
Note that NET-Builder has no access to or control over these cookies that are used by third-party advertisers.
NET-Builder's Privacy Policy does not apply to other advertisers or websites. Thus, we are advising you to consult the respective Privacy Policies of these third-party ad servers for more detailed information. It may include their practices and instructions about how to opt-out of certain options.
You can choose to disable cookies through your individual browser options. To know more detailed information about cookie management with specific web browsers, it can be found at the browsers' respective websites. What Are Cookies?
Another part of our priority is adding protection for children while using the internet. We encourage parents and guardians to observe, participate in, and/or monitor and guide their online activity.
NET-Builder does not knowingly collect any Personal Identifiable Information from children under the age of 13. If you think that your child provided this kind of information on our website, we strongly encourage you to contact us immediately and we will do our best efforts to promptly remove such information from our records.
This Privacy Policy applies only to our online activities and is valid for visitors to our website with regards to the information that they shared and/or collect in NET-Builder. This policy is not applicable to any information collected offline or via channels other than this website.
By using our website, you hereby consent to our Privacy Policy and agree to its Terms and Conditions.